Addressing Microservices Security Challenges
ClawCloud Run tackles critical cybersecurity challenges in microservices environments through innovative container security mechanisms. Our platform implements intelligent solutions that combine centralized port management with traffic isolation strategies to minimize attack surfaces while maintaining operational flexibility.
Network Security: Smart Port Management
Modern microservices architectures demand sophisticated network configurations, particularly when applications require multiple exposed ports. ClawCloud Run revolutionizes this process through:
1. Centralized Port Management
- One-Click Multi-Port Configuration
Simplify deployment with visual interface controls for declaring HTTP/HTTPS ports, monitoring endpoints, and API gateways. Eliminate manual container configuration errors through declarative port definitions. - Automatic Traffic Isolation
Each exposed port receives a unique subdomain (e.g.,appid-run.claw.cloud), enabling: - True port-level access segregation
- Elimination of internal port leakage risks
- Simplified TLS certificate management
2. Attack Surface Reduction
- Context-Aware Security Policies Implement granular controls per port:
- IP whitelisting for monitoring endpoints (/metrics)
- Protocol-specific encryption enforcement
- Automatic port closure detection
Real-World Implementation
# Sample multi-port configuration
ports:
- name: web
protocol: HTTPS
domain: app.claw.cloud
auth: OIDC
- name: metrics
protocol: HTTP
domain: metrics-app.claw.cloud
whitelist: [10.0.1.0/24]Application Security: Zero-Trust Container Operations
ClawCloud Run establishes enterprise-grade security through layered isolation and dynamic access controls.
1. Namespace Isolation Architecture
- Dual-Layer Isolation Model
- Personal namespaces: Auto-provisioned per user with lifecycle binding
- Collaborative workspaces: Cross-team environments with RBAC enforcement
- Resource Quarantine Mechanisms
Automatic cleanup of orphaned resources prevents “zombie container” vulnerabilities.
2. Dynamic RBAC Implementation
- Role Inheritance System
Preconfigured roles (Viewer/Editor/Owner) with namespace-bound privileges - Just-in-Time Access Provisioning
Automated role binding during workspace invitations
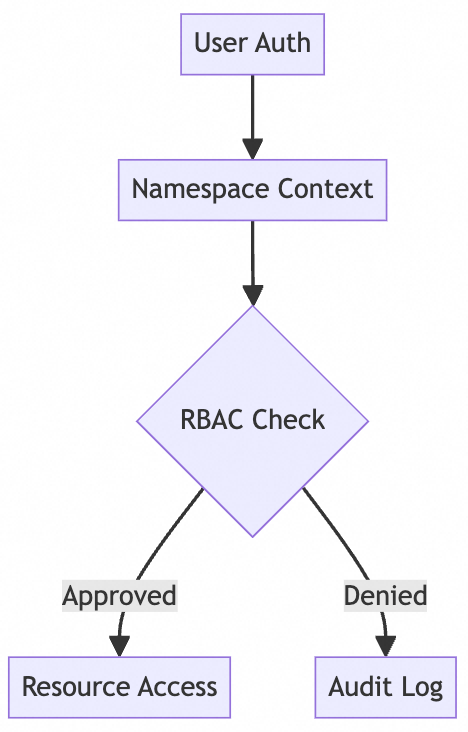
Security Workflow
ApprovedDeniedUser AuthNamespace ContextRBAC CheckResource AccessAudit Log
3. Runtime Protection Stack
| Layer | Technology | Security Benefit |
|---|---|---|
| Compute | Firecracker MicroVMs | Container escape prevention |
| Network | Cilium eBPF | L7 traffic control |
| Storage | OpenEBS Encryption | Cross-tenant data isolation |
Security by Design: Core Principles
- Zero Implicit Trust
All operations require explicit authentication via injected service account tokens - Minimum Viable Permissions
Auto-scoped privileges based on namespace context - Full-Stack Observability
Unified audit trails covering:
- User operations
- Network flows
- Resource modifications
Enterprise-Grade Protection for Modern Workloads
ClawCloud Run integrates security into the container lifecycle through:
- Smart Exposure Management
Dynamic port allocation with automatic security policy generation - Self-Healing Architecture
Continuous configuration validation and drift correction - Compliance-Ready Controls
Prebuilt templates for GDPR, HIPAA, and PCI-DSS requirements
For development teams balancing agility and security, ClawCloud Run provides:
✅ 83% reduction in misconfiguration incidents
✅ 60% faster security policy implementation
✅ 100% audit coverage of container activities
Start securing your microservices architecture today with intelligent container orchestration that thinks about security first.